MTS MBlaze Ultra Wi-Fi/ZTE AC3633 Multiple Vulnerabilities
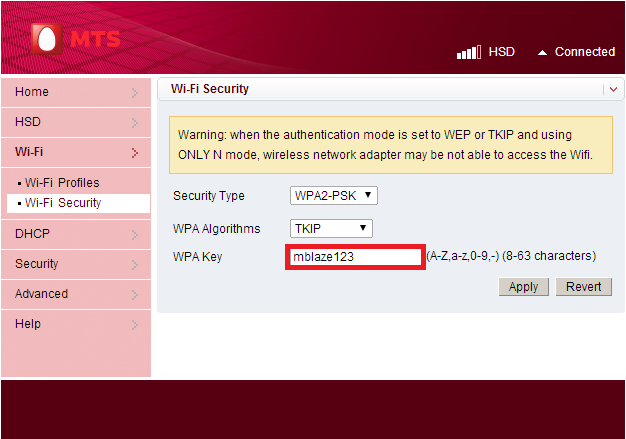
Recently a Device MTS MBlaze 3G Plus Wi-Fi USB Modem.The interesting thing is that, it allowed up to 5 devices to connect to it via Wi-Fi. So it appears to me as a fast, cheap and portable broadband alternative. This device is manufactured by ZTE, a Chinese multinational telecommunications equipment and systems company.- One thing I noticed is that Wi-Fi WPA/WPA2/WEP Key is shown as plain text in the text box.
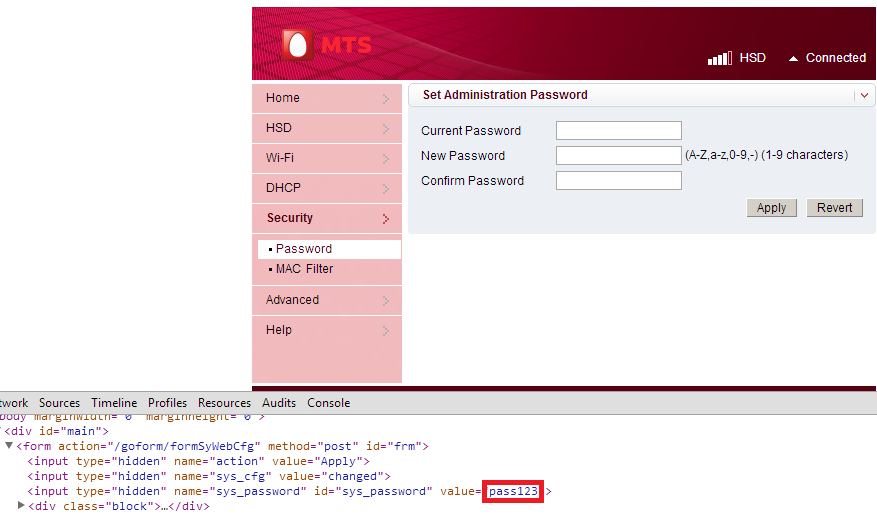
- After some digging outs, it was found that the passwords are hard coded
in the source code. The router web interface password is hard coded in
the password reset page.
 The worst thing was that the session maintaining cookie used by the router web interface is static. This Cookie (iusername=logined)
is all you need to get an authenticated session. As this session cookie
is constant all the times, simply setting the cookie will give access
to protected pages in the web interface.
The worst thing was that the session maintaining cookie used by the router web interface is static. This Cookie (iusername=logined)
is all you need to get an authenticated session. As this session cookie
is constant all the times, simply setting the cookie will give access
to protected pages in the web interface.
Putting it all together, A quick dirty python POC exploit for MTS MBlaze Ultra Wi-Fi / ZTE AC3633 that can do the following things.
- Bypass Login
- Extract IP Address, Subnet, Gateway Information
- Steal Router Credentials
- Steal Wi-Fi WPA/WPA2/WEP Key
- Reset Password without old password and valid session
- List out the CSRF affected pages
Attack Scenario
Initially attacker will exploit CSRF and make the victim to visit a page containing the following IFRAME<iframe src="http://192.168.1.1/goform/formSyWebCfg?wl_encryption_protocol=3&wl_wpa_psk_mode=0&wl_wpa_psk_key=xboz&
wl_auth_mode=0&oem_cfg=changed&action=Apply" width="0" height="0">
Now the Wi-Fi Key is changed to xboz. From this point, the attacker can connect to the Wi-Fi network and execute the exploit to gain access to the MTS device.
Download Exploit
Exploit
Rishabh Jain(Rjceh0815) A Person Who Loves To play with Security and find the loop holes in that.
Graduated in B.Tech Information Technology
# EC Council Certified Security Analyst (E|CSA)
# Certified Ethical Hacker (C|EH)
# Cisco Certified Network Associate (CCNA)
Skilles
* Knowledge of WebDesigning
* Languages: C,C++,.NET,C#,PHP
Follow him @ Twitter | LinkedIn | Google+ | Email | Facebook Profile